Cloud security is among the top topics under deliberation when most organizations migrate their workloads, after all security loopholes can leave their infrastructure prone to vulnerabilities. Choosing the right Cloud Service Provider (CSP) becomes critical to enjoy long-term success with improved security and reduced downtimes. There are many players in the market such as, Microsoft, Amazon, and Google and other smaller players offering custom services according to their users. However, asking the right questions while opting for any CSP becomes critical in finding the right stack of security features.
Compared to traditional security practices, cloud tech brings ensures the complete security of any workload deployed. However, different industries have varied security and compliance demands, and there is always room for improvement. Hence, all the cloud service providers are constantly boosting their security features in order to bring cloud services to all sectors, from healthcare to fintech.
Despite the offerings provided by CSPs, native security features offered by hyperscalers are still proving inadequate. The main reason behind these security shortcomings is the varied demand and the difficulty in adding the security element to automated cloud workloads due to their complex nature. Although the native security measures are robust, there are a lot of verticals where they might prove to be insufficient, such as:
- High-level data breaches
- Inadequate access controls
- Account hijacking
- Inside threat
- Insecure APIs
- Metastructure failures
- Reduced visibility
- Poor control plane
- Abuse of cloud services by malicious elements
These dangers need added services on top of native security measures to ensure you remain in control of your cloud and forego the worries about threats to your infrastructure. In this article, we’ll discuss a few common security shortcomings and how Centilytics helps you plug them.
Lack of Security Audits
All major CSPs such as Microsoft Azure or Amazon Web Services offer their own security audits, but these audits are not adequate for an organization hosting their business-critical workloads on the cloud. The audits offered by these CSPs help users troubleshoot problems or reduce the chances of a potential one, all the while helping users improve their performance and allowing them to automate actions. All this seems great, but this is easier said than done. Forget automation; even using the audit to troubleshoot the problems requires subject-matter experts.
Centilytics provides you a simple console with a clear and intuitive UI to help everyone access and manage their cloud, irrespective of their cloud expertise. With our intelligent console, you can identify loopholes, assess risks, and remediate vulnerabilities for not just a single cloud, but also for multi-cloud infrastructures. Not only this, we also offer:
- Security Overview
- 300+ security checks
- One-click fixes
- Multiple Compliances management: GDPR, HIPPA, PCI, NIST, ISO, CIS, CSA, Trusted Advisor, Azure Advisor.
Step 1: Use actionable insights to ensure complete control over your business processes framework through Identity and Access Management.

Step 2: Eradicate malicious activities such as hacking, Distributed Denial-of-Service attacks, and much more by implementing security to your EC2 instances.
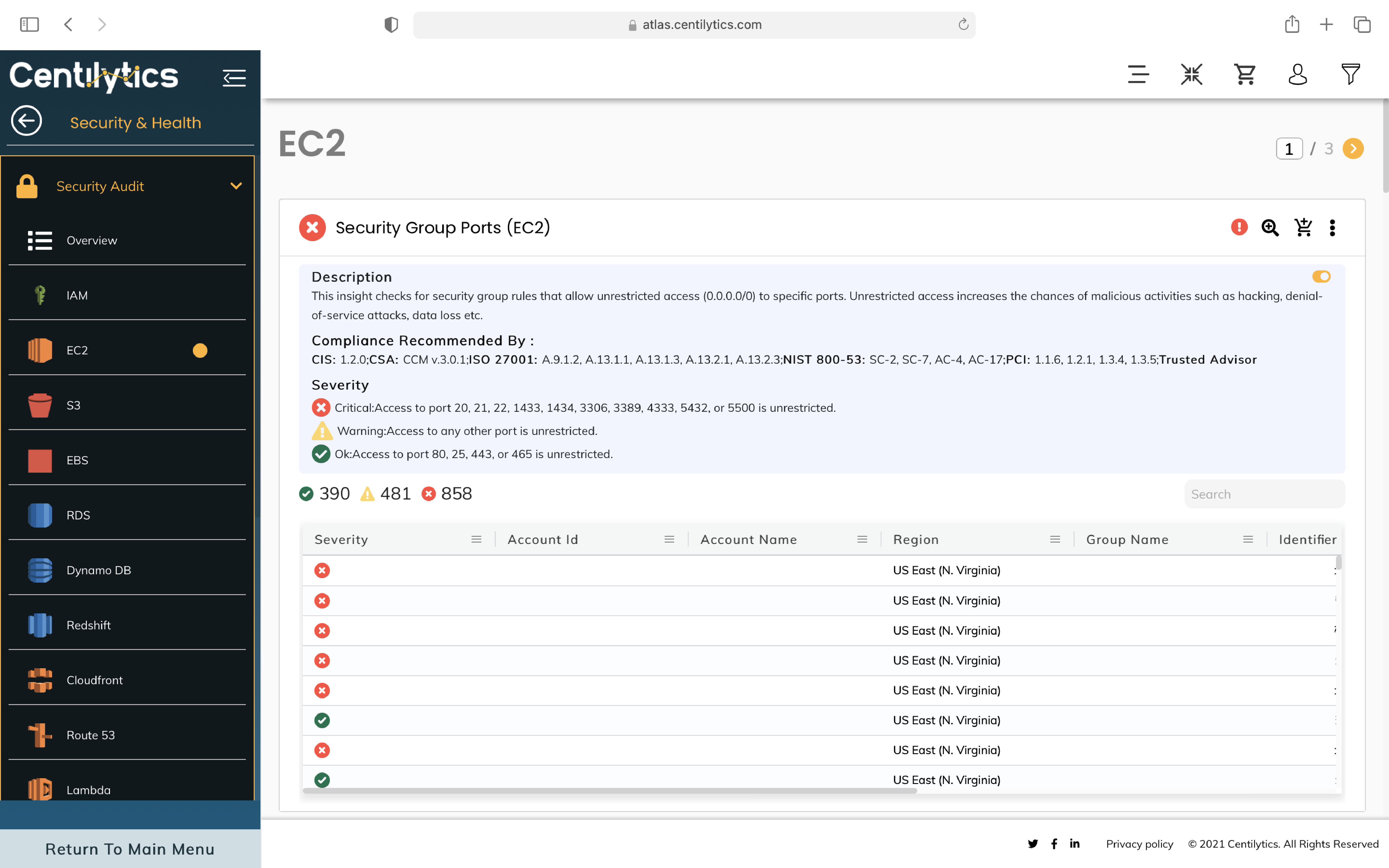
Fault Tolerance
Organizations opting for cloud to deploy their workloads have always faced the uncertainty of unexpected downtimes that can lead to business-threatening losses. Due to their inability to provide bespoke solutions to every single organization, CSPs cannot provide total fault tolerance to all their users. Centilytics’ Fault Tolerance module helps users reduce the impact of the uncertainties with multiple health checks, various availability zones, auto-scaling recommendations, and many more.
Not only this, Centilytics also offers disaster recovery readiness using fault tolerance insights such as snapshot age, backups, AMI age, etc.
Step 1: Check the age of your EC2 AMI age based on various severity levels.

Step 2: Use Fault Tolerance Module to check the current status of multiple instances, deployments, and more from a single dashboard.

Optimizing Performance
Inefficient use of resources deployed in the cloud infrastructure may lead to performance degradation in the long run. The tools and modules offered by CSPs often try to correct this shortcoming but their complex nature leads to the users feeling overwhelmed and not being able to optimize their resources. Centilytics’ Performance Optimizer ensures that your workloads are deployed efficiently and are running at optimum levels across the infrastructure. We also provide dedicated security checks to help users track their over- or under-utilized instances and ensures applications make the most out of the provisioned resources.
Step 1: Keep your performance at optimum level through ensuring the usage of resources based on their severity.
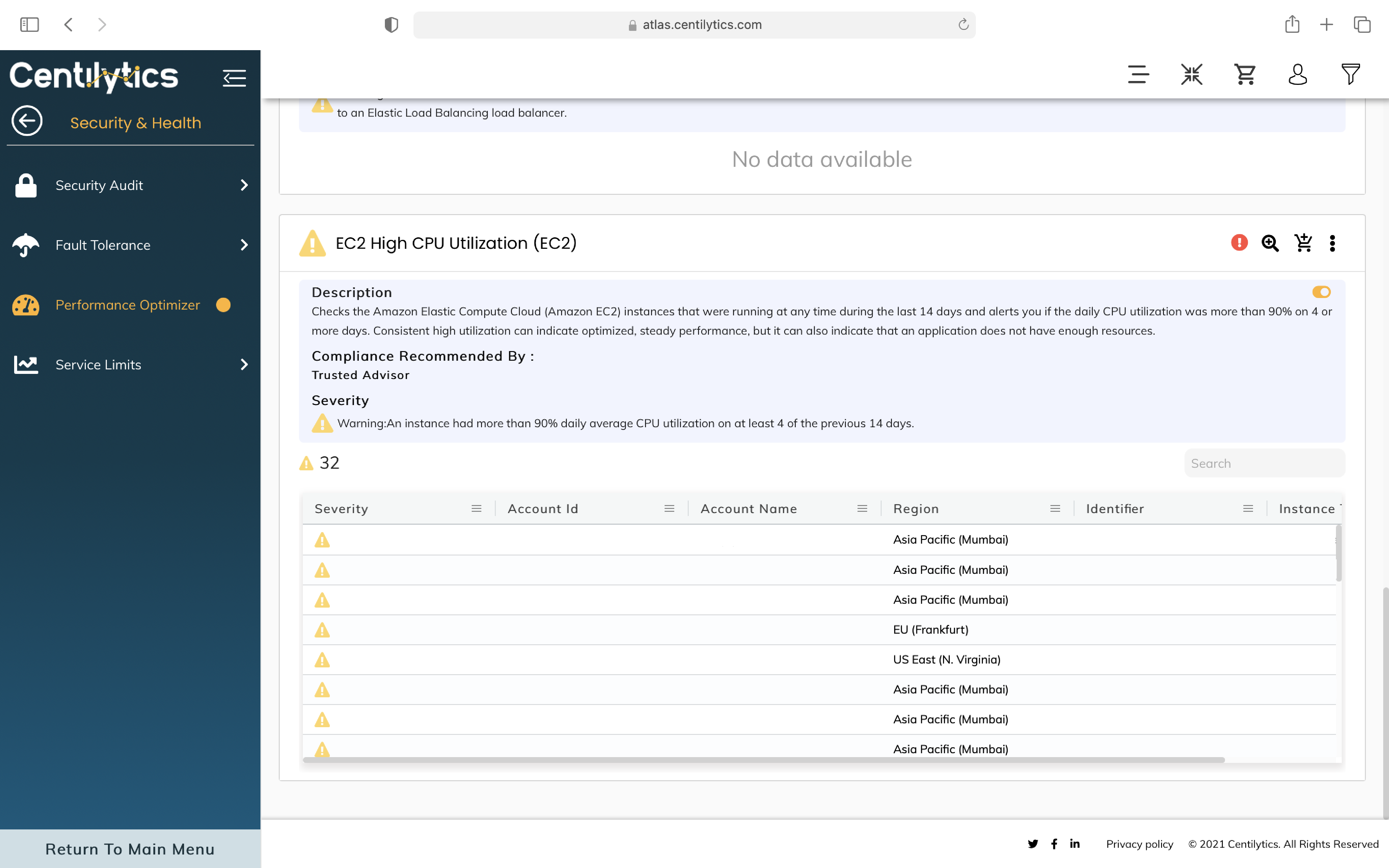
Step 2: Ensure a limited number of rules are applied to a group to leverage superior performance.

CSPs implement a default limit to services opted by the user to avoid misuse, these limits can be increased by the organization depending on whether it’s a soft or hard limit. These services are an integral part of how CSPs manage their offerings, so much so that any breach in these limits can lead to failure in performing a particular action and can even prevent the scalability of your cloud infrastructure. Centilytics’ Service Limits module helps the users track and manage such service limits with actionable insights to make relevant changes based on the usage from the console then and there.
Step 1: Ensure correct deployment of service limits in your multi-cloud infrastructure.
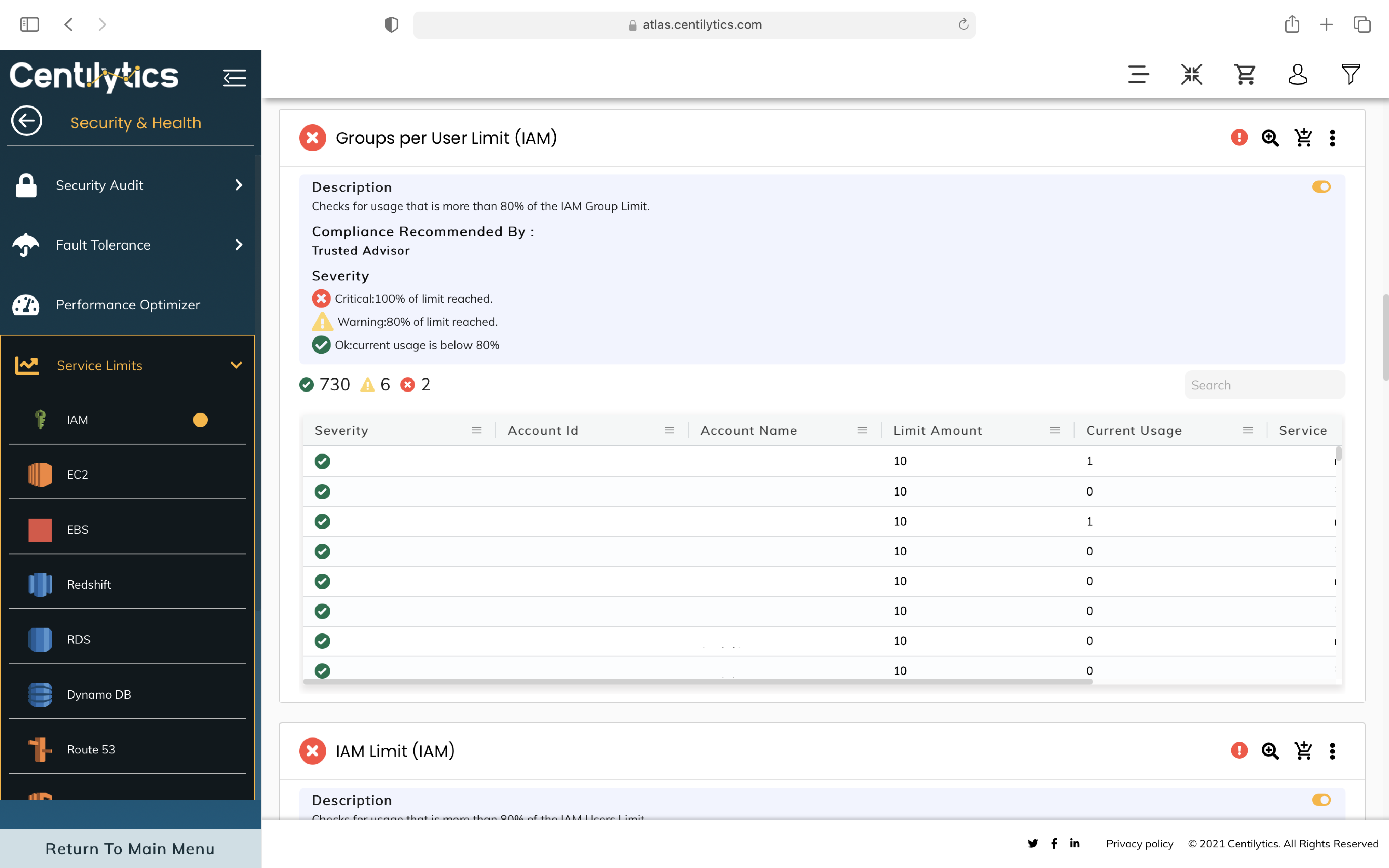
Step 2: Get a holistic view and check for usage in IAM group limits, role policy size limits, and much more.



